Ransomware…
What is it, What Happens, How Can We Protect Ourselves?
Ransomware is a type of malicious software, or malware, that prevents you from accessing your computer files, systems, or networks and demands you pay a ransom for their return. Ransomware attacks can cause costly disruptions to operations and the loss of critical information and data.
You can unknowingly download ransomware onto a computer by opening an email attachment, clicking an ad, following a link, or even visiting a website that’s embedded with malware.
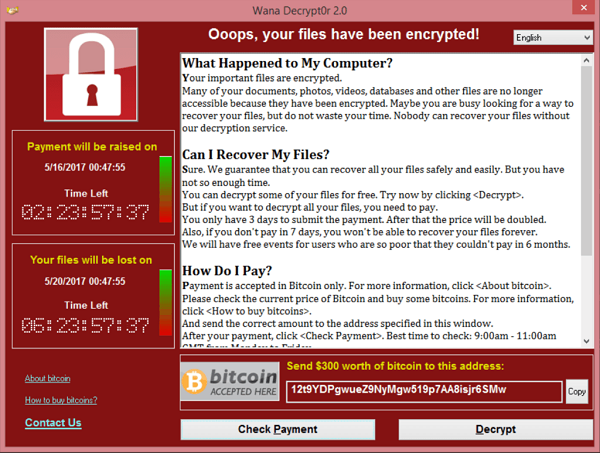
Once the code is loaded on a computer, it will lock access to the computer itself or data and files stored there. More menacing versions can encrypt files and folders on local drives, attached drives, and even networked computers.
Most of the time, you don’t know your computer has been infected. You usually discover it when you can no longer access your data or you see computer messages letting you know about the attack and demanding ransom payments.
Ransomware attacks doubled in frequency in 2021 according to the Verizon Data Breach Investigation Report and from January to July 2021 the FBI reported a 62% increase in Ransomware complaints made to them.
Cybercriminals typically target businesses and governments in hopes they’ll pay big bounties to release files and restore critical systems. But ransomware attacks happen to regular computer users, too. “When a consumer is a victim with ransomware, it means the cybercriminal has something they can demand payment for, such as your documents, including tax returns, or maybe important photos and videos [like home movies] that are now encrypted,” says Steve Grobman, chief technology officer of McAfee, a leading cybersecurity company. “You may see an email that says you need to pay if you want these files back. Or in other cases you’re told your entire computer is locked and unless you pay, they’ll make it essentially unusable,”
Fake ransomware,” a demand for payment without a criminal accessing your files, is also a problem. So what should you do?
Don’t take any actions before a technology and/or law enforcement expert is involved, as it could make the situation worse.
- What options do you have to recover your files other than paying?
- Do you have duplicate files somewhere else, such as on a hard drive not connected to your computer?
- Do you need the hijacked files or care if they are revealed?
The next step is to confirm, if possible, that ransomware has actually been installed on your computer. If the extortionists claim they have all your emails, have they supplied a sample to prove it?
Don’t accept unsolicited help for your problem. “We’ve seen a one-two punch, where you get a notification of ransomware, followed up by a scam that looks like it comes from a trusted source like Microsoft or McAfee that says, ‘We’ve detected you’ve become a victim of ransomware. We’re here to help. Please call this number and allow our technicians to remote control your computer,’ ” Grobman says. “Never, ever act on any of those emails.” Legitimate software vendors won’t contact customers that way.
If you are confident in your technical skills, consider checking the website No More Ransom to see if you have been infected by ransomware with a known solution or decryption key. That way, you can unlock your files without paying. No More Ransom was launched in 2016 with the goal of helping victims retrieve their encrypted data without losing money.
Take a look at this video explaining Ransomware in simple terms
Protection against Ransomware – Preventing Infection

- Never click on unsafe links: Avoid clicking on links in spam messages or on unknown websites. If you click on malicious links, an automatic download could be started, which could lead to your computer being infected.
- Avoid disclosing personal information: If you receive a call, text message, or email from an untrusted source requesting personal information, do not reply. Cybercriminals who are planning a ransomware attack might try to collect personal information in advance, which is then used to tailor phishing messages specifically to you. If in any doubt as to whether the message is legitimate, contact the sender directly.
- Do not open suspicious email attachments: Ransomware can also find its way to your device through email attachments. Avoid opening any dubious-looking attachments. To make sure the email is trustworthy, pay close attention to the sender and check that the address is correct. Never open attachments that prompt you to run macros to view them. If the attachment is infected, opening it will run a malicious macro that gives malware control of your computer.
- Never use unknown USB sticks: Never connect USB sticks or other storage media to your computer if you do not know where they came from. Cybercriminals may have infected the storage medium and placed it in a public place to entice somebody into using it.
- Keep your programs and operating system up to date: Regularly updating programs and operating systems helps to protect you from malware. When performing updates, make sure you benefit from the latest security patches. This makes it harder for cybercriminals to exploit vulnerabilities in your programs.
- Use only known download sources: To minimize the risk of downloading ransomware, never download software or media files from unknown sites. Rely on verified and trustworthy sites for downloads. Websites of this kind can be recognized by the trust seals. Make sure that the browser address bar of the page you are visiting uses “https” instead of “http”. A shield or lock symbol in the address bar can also indicate that the page is secure. Also exercise caution when downloading anything to your mobile device. You can trust the Google Play Store or the Apple App Store, depending on your device.
- Use VPN services on public Wi-Fi networks: Conscientious use of public Wi-Fi networks is a sensible protective measure against ransomware. When using a public Wi-Fi network, your computer is more vulnerable to attacks. To stay protected, avoid using public Wi-Fi for sensitive transactions or use a secure VPN service.

