It’s important to understand ways we can enhance our digital security and safeguard our personal information.
Virtual Private Networks, 2 Factor Authentication and Password Managers are all tools we can use.
Let’s take a brief look at each of them…

What is 2FA ?
Two-factor authentication (2FA) is a security system that requires two separate, distinct forms of identification in order to access something. The first factor is a password and the second commonly includes a text with a code sent to your smartphone, or biometrics using your fingerprint, face, or retina. Email can be used for it as well but is less popular.
But this two-factor authentication mechanism has its downsides. If email is used to confirm the login, and the password for logging into it is the same as for the account you’re trying to protect, you’ll get very limited extra security. An attacker who knows the account’s password is certain to try that password to sign in to your email too — thus getting the one-time validation code.
Validation through phone number — whether by SMS or voice call — has a different problem: it’s easy to lose access to it. Sometimes users simply forget to top up their phone account, or they lose the phone or change the number.
It’s also possible for criminals to access the telecom operators and obtain a SIM card with the victim’s phone number, thus getting access to validation codes.
One of the most recent, and in our opinion, more secure 2FA methods is by One-time codes from an authenticator app. Single use one time codes (normally with a “time out” feature) are produced by the app which runs on your smartphone or mobile device. Popular versions include the Microsoft Authenticator and Google Authenticator although there are others available. You need to research the options available for windows, ios, android, macOS etc etc that are applicable to your devices.
In summary, 2FA is a vital tool in our armory to protect against unauthorized account access and we should be using some form of it wherever possible.
What is a VPN ?
Do you worry about online security while using public Wi-Fi? Or fear that you might get hacked when using an insecure connection and someone will steal all your details? VPN, which stands for virtual private network, protects its users by encrypting their data and masking their IP addresses. This hides their browsing activity, identity, and location, allowing for greater privacy and security. This can be used on computers and mobile devices. It’s particularly useful when using public wi-fi or any unprotected network for added security.
A VPN acts as a tunnel through which all your data goes from your location to your destination. It’s all properly encrypted and secure so that any outside party can’t see what data you are transferring.
There are many advantages to using VPNs, such as:
Privacy
Anonymity
Security
Encryption
Masking your IP address so you can’t be traced
Everything on the internet is tracking you. Website and web servers that you use or visit know your IP and location. That can be used to their advantage and every time you visit the same website, they will know that it’s you, and they will track your usage and your behavior. This isn’t necessarily a good thing since you are giving them a lot of information without knowing what.
A VPN can help keep your identity anonymous so you don’t need to worry about identity leakage or any kind of tracking activity.
Using a VPN can keep your identity safer and also keeps your data encrypted while you browse the internet. As a result, it enhances security and the chances that someone might hack you will be lower. It will also keep you safe when you are using any public Wi-Fi or browsing websites which are not secure.


What is a Password Manager ?
A password manager (or a web browser) can store all your passwords, so you don’t have to worry about remembering them. This allows you to use unique, strong passwords for all your important accounts (rather than using the same password for all of them, which you should never do).
Once you’ve logged into the password manager using a ‘master’ password, it will generate and remember your passwords for all your online accounts. Many password managers can also enter your passwords into websites and apps automatically, so you don’t even have to type them in every time you log in.
If you’re using a shared computer outside your home (for instance, at a college or library) you should never save your password in a browser.
If you’re sharing a computer in your household, either with family or housemates, then you’ll have to think about who else could access the computer (and therefore to your saved passwords), and decide if you’re ok with this.
There are many “Password Manager” apps available that produce random, lengthy and supposedly secure passwords for different websites you use all sitting beneath your “master” password. Whilst convenient, due to their configuration we probably won’t have reason to remember them and therefore if they are hacked it’s a major problem.
Hackers know that compromising a password manager is like getting the keys to the castle. If a password manager gets compromised, attackers gain access to all stored passwords at once, which means they can walk into any secured environment or impersonate any user, circumventing all cybersecurity defenses.
There are many pros and cons which need to be carefully considered when using password managers.
So What Have We Learnt?
We know that we need to use as many tools as possible to keep ourselves safer in the digital world. Most have pros and cons and the trade off is usually between convenience or ease and taking the time to educate ourselves and perhaps use the more time consuming method that results in more robust protection.
VPN’s should be in everyone’s tool box and be deployed always (at work our companies will usually have their own methods deployed).
Similarly, 2FA should be used in one of its forms or another wherever it’s available to us. It’s a really good line of defense and in more and more instances we don’t have the option NOT to use it. Vendors and websites are requiring its implementation.
Password Managers provide a lot more food for thought and rushing to the cheapest or most easily available option may bring headaches down the road. We’re not saying they don’t have value but that they do require more investigation relative to our personal requirements.


Download the PDF to share…
Please share this with colleagues, employees and anyone else that you care to! The better informed we are, the safer we are! Click on the button below…
Here’s a video to remind us of what a Phishing attack is…
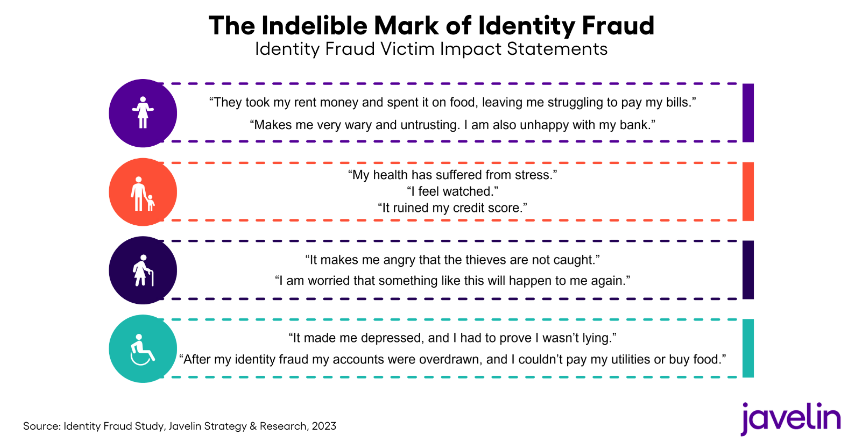
If you think that Identity Theft is still a vague concept that has only minimal impact, take a look at some Victim Statements from a recent Javelin study…